Newly Discovered Flaw in iCloud Private Relay Service Leaks User’s IP Address – Apple-cnBeta.COM
A flaw has been discovered in Apple’s newly launched iCloud private paging system, which exposed a user’s IP address when certain conditions are met, thus destroying the core value of the functionality. As researcher and developer Sergei Mostevenko explained in this week’s blog post, a flaw in handling WebRTC by private relays can “leak” a user’s real IP address, which is understood by the FingerprintJS website as proof.
being able to:
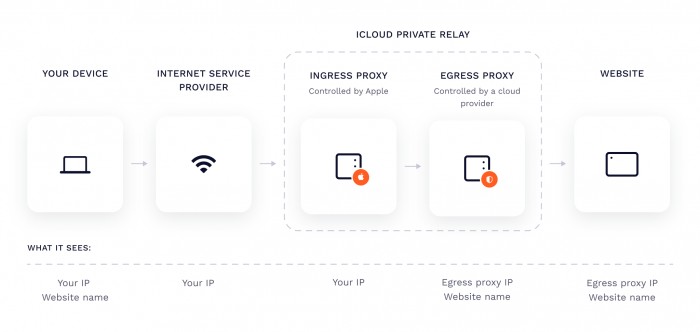
Private Relay, announced at the Worldwide Developers Conference in June, promises to prevent third parties from tracking users’ IP addresses, locations and other details by directing Internet requests to two separate relay stations operated by two different entities.An appleThe company said it was configured to use anonymous IP addresses for Internet connections via special relays, assigned to a user’s region, but did not reveal its exact location or identity.
In theory, the website should only see the export agent’s IP address, but the user’s real IP address will be reserved in some WebRTC connection scenarios, which can be detected by some smart code.
As explained by Mostsevenko, the WebRTC API is used to facilitate direct communication on the network without the need for an intermediary server. WebRTC, which is deployed in most browsers, relies on the Interactive Connection Creation (ICE) framework to connect users. One browser collects ICE filters and uses potential communication methods to find and establish a link to the second browser.
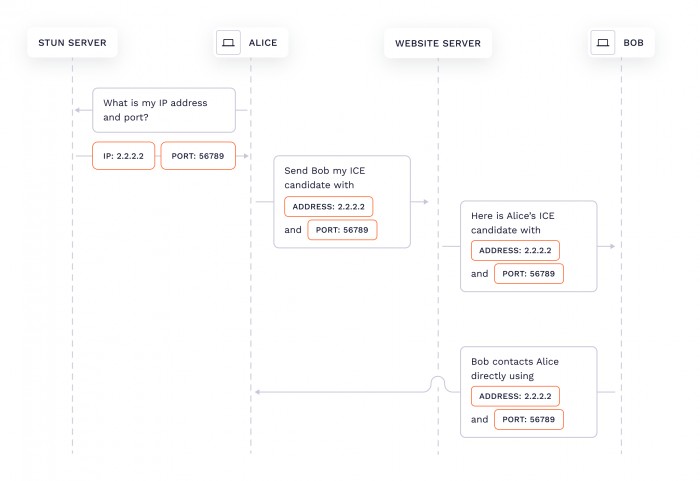
The vulnerability appears in the server reflexology filter, which is a filter used by the Server NAT Session Traversal (STUN) tool to communicate with machines behind NAT. Network Address Translation (NAT) is a protocol that enables multiple devices to access the Internet through a single IP address. The important thing is that the STUN server shares the user’s public IP address and port number.
Since Safari does not proxy STUN requests through a private iCloud relay, the STUN server knows your real IP address. This is not a problem in itself, because they have no other information; however, Safari passes ICE filters containing IP addresses true to the JavaScript environment,” said Mostivenko. Then after the de-identification is complete, the problem of parsing your real IP address becomes an ICE candidate – and this can easily be done through a web application.
According to the researcher, the user’s IP address can be collected by creating a connection object to the STUN server, collecting ICE candidates and analyzing their values.
FingerprintJS reported the vulnerability to Apple, and pushed the company to fix the latest macOS Monterey beta released this week. However, the vulnerability has not been patched in iOS 15.
Learn more:
https://fingerprintjs.com/blog/ios15-icloud-private-relay-vulnerability/

Subtly charming zombie buff. Amateur analyst. Proud tvaholic. Beer fanatic. Web expert. Evil troublemaker. Passionate internet maven. Gamer. Food evangelist.