Dark web, illegal traffic in personal data is on the rise

Accounts linked to online games and live streaming remain the most vulnerable to data theft

In the wake of the pandemic, an expanding audience of users has begun to use the web extensively, which provides more opportunities for hackers to carry out their criminal activities. Compared to the first half of 2020, in fact, in the second half of the year, the number of Italian users who received a warning about a cyber attack on their personal data increased by 56.7%. In particular, the data refers to alerts about information on the dark web (a group of web environments that do not appear through normal internet browsing activities and require specific browsers or targeted searches), which are roughly twice that of a web audience.
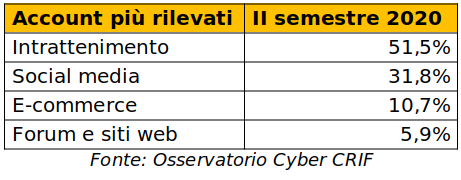
In general, accounts linked to entertainment sites (especially online games and live broadcasts) remain the most vulnerable to personal data theft (51.5% of all cases).
On the other hand, social networks saw a significant increase in risks, jumping from 1.6% to 31.8%.
These are some of the evidence that emerged from the Cyber Observatory established by CRIF, which aims to analyze the vulnerability of people and companies to cyberattacks and explain the main trends related to the exposed data in open web and dark web environments, the type of information, the areas in which the data traffic is concentrated and the countries most exposed to it, in addition to To provide some ideas for dealing with cyber risks in a conscious manner.
The cyber observatory data raises awareness of the vulnerability of private and business data. The use of digital technology has seen an acceleration due in large part to the epidemic, and has introduced the habits of purchasing and using services for many people. At the same time, many companies have started offering their products and services through e-commerce, and therefore they necessarily have to start a website and manage orders online. However, like all news, the side risks should not be underestimated. They are brand new for many. ‘ – He explains Beatrice Robini, CEO de Creve.
Italy is among the worst affected countries
In view of the ranking of countries most affected by the phenomenon of e-mail and password theft on the Internet, the United States of America, Russia, France and Germany came in the top, followed by the United Kingdom and Italy, which ranked sixth in general. The top ten were completed by Poland, the Czech Republic, Japan and Brazil.
Another area of investigation in the cyber observatory is that which is devoted to ranking the continents most vulnerable to exchanging illicit credit card data. This ranking is led by North America, followed by Europe and Asia, but with a large gap from the first in the classification. At the bottom of the ranking we find Africa and Oceania. Among the individual countries that participated the most, we find the United States at the top, followed by France and Brazil, who completed the podium, while Italy ranks 11th.
The victims are usually men, in 65.6% of cases, between the ages of 41 and 60, with nearly 54% of the total. There are undoubtedly some behaviors that can benefitally mitigate risks. For example, on the consumer side, the point of interest is represented by the ways in which we identify and manage passwords associated with different accounts and the interest with which we respond to emails, messages, or phone calls. On the business side, which includes a website or e-commerce site, it is important to ensure protection systems but also to promptly intercept potential security holes resulting from legacy software or service configurations, ”Rubeny adds.
The type of data circulating on the dark web
Moreover, according to the Observatory, in the second half of 2020, the personal data that is mainly circulating on the dark web, and thus more vulnerable, are passwords, individual or company email addresses, user names, and phone numbers. These valuable contact details can be used to attempt fraud, for example through phishing or phishing. However, there is no shortage of sharing data of financial value, such as credit cards and IBANs.
It is even more interesting to note the main groups of data that are intercepted on the web. Emails are always associated with a password (in 96.3% of cases), while cases where phone numbers appear with passwords are significantly reduced (-52%).
If those on the dark web are mostly personal email accounts, there is a certain acceleration at the forefront of breaches on business accounts, which within 6 months saw an increase of + 27.8%.
Regarding credit card data, in addition to the number, there are always resumes and expiration dates (in 98.6% of cases) and in 20.8% of cases the name and surname of the cardholder is also found.
Analyze your most used passwords
According to an analysis of passwords discovered on the dark web, in the first place among the top 10 most used passwords in the second half of 2020 is “123456”, followed by “123456789” and then “qwerty”.
So these are very simple combinations of numbers and letters, which are easy for hackers to intercept. On the other hand, the use of these basic passwords reveals the lack of experience or laziness of a portion of web users, who often do not follow the basic rules to protect themselves from potential intrusions, for example by choosing long, different passwords for any important account, with groups of Letters, numbers and symbols have nothing to do with personal information.
It will also be important for users to activate two-factor authentication, wherever possible, to prevent hackers from entering accounts even if they discover their login and password information, as it is advised that close attention be paid to using public WiFi networks, so that the most secure password can be intercepted, and the risks associated with storing Credentials on public or shared computers.

Friendly alcohol advocate. Future teen idol. Beer aficionado. Amateur music fanatic. Food guru.